SSO Configuration
Use the SSO Configuration screen to manage settings related to Just-In-Time (JIT) provisioning and SAML Mapping.
When Single Sign-On (SSO) is configured for an organization, all authentication requests are routed through the third-party identity provider (IdP) and users cannot log in directly to BigPanda. If a user does not have a valid session with the IdP, they are redirected to the SSO login page where they may be prompted for their IdP login information. The IdP then passes the successful identity authorization back to BigPanda, logging the user into BigPanda.
SSO with Just-In-Time (JIT) Provisioning automatically creates user accounts in BigPanda when users first log in via SSO, eliminating the need for manual account creation. Account creation is based on rules and properties defined in your SSO provider’s object.
With JIT Security Assertion Markup Language (SAML) mapping, you can also configure roles to automatically sync to BigPanda each time a user logs in.
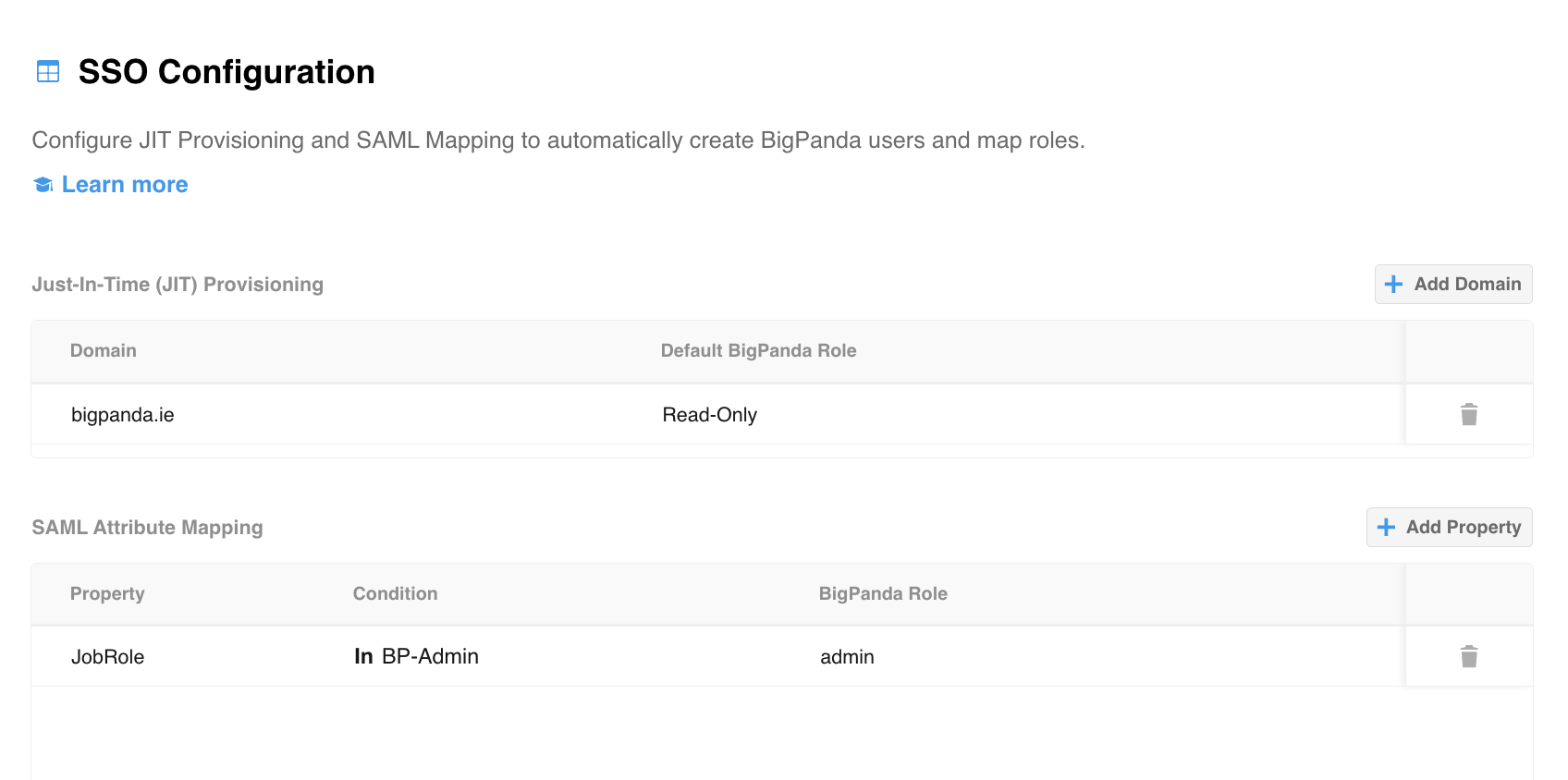
SSO Configuration Screen
Key Features
The benefits of SSO with JIT configuration include:
- Added security controls through the IdP, such as two-factor authentication or login restriction via a corporate authentication tool.
- Automatic role mapping from your IdP to BigPanda.
- Simplified password management and reduced password fatigue.
- Easier user management, onboarding, and offboarding.
Relevant Permissions
Roles with the following permission can access the SSO Configuration section in BigPanda Settings:
| Permission Name | Description |
|---|---|
| Single Sign-On | View, select, and configure a Single Sign-on provider in BigPanda Settings. |
You can adjust permission access levels by selecting either the View or Full Access option. To learn more about how BigPanda's permissions work, see the Roles Management guide.
Before You Start
Before configuring JIT settings and SAML Attribute Mapping, you’ll need to enable SSO for your organization. See the Single Sign-On documentation for SSO requirements, setup instructions, and more information.
After you have SSO enabled, configure the BigPanda SAML properties in your SSO provider console.
JIT Provisioning
JIT Provisioning allows you to define the domains associated with your IdP, and select default BigPanda user roles for newly created accounts from each SSO domain.
With JIT Provisioning enabled, when users first sign in to BigPanda via the SSO, a new account will be created with the default role set for the domain.
To configure JIT Provisioning:
- Within BigPanda, navigate to Settings > SSO Configuration.
- Click Add Domain.
- In the Add Domain window, enter your Domain and select a Default Role from the drop-down menu.
- Click Create.
SAML Attribute Mapping
You can use properties from your IdP to automatically map roles to an account in BigPanda whenever an existing user logs in.
SAML Attribute Mapping overrides roles that were manually assigned to BigPanda accounts. When you change an account’s role settings in the active directory, BigPanda automatically updates the corresponding user account the next time they log in to BigPanda.
To ensure that roles are mapped appropriately in BigPanda, you'll need to confirm that the role exists in the SAML properties for each user.
Roles
If no role is sent in the SAML attributes for a user, the BigPanda role defined for the domain configured in the JIT Provisioning section will be used.
Name attribute capitalization
Name attributes must be formatted as
firstNameandlastName. Name attributes sent with other case formatting will be created with their email address instead of a full name.
Configure SAML Attribute Mapping in Your IdP
To use SAML Attribute Mapping in BigPanda, you must first set up SAML Attribute Mapping in your IdP. Reference the SAML documentation for your IdP, or reach out to your IdP admin for support. Below you’ll find documentation for the most popular IdPs:
Microsoft Entra ID
If you are using Microsoft Entra ID (Formerly Azure AD), you will also need to manually set firstName and lastName claims since they are not provided by default. See the BigPanda Microsoft Entra ID documentation for more information.
Configure SAML Attribute Mapping in BigPanda
JIT Provisioning
JIT Provisioning must first be configured to use SAML Attribute Mapping.
To configure SAML Attribute Mapping:
- Within BigPanda, navigate to Settings > SSO Configuration.
- Click Add Attribute.
- In the Add Mapping window, define the following fields:
| Field | Description |
|---|---|
| Property Name | Enter the name of the SAML attribute. |
| Multiple Attributes or Single Attribute | If the SAML attribute is from a group, select Multiple Attributes. If the SAML attribute is not from a group, select Single Attribute. |
| Contains or Equals. | Enter the name of the attribute that will be mapped from your SAML properties. This field is not case-sensitive. If you are mapping Multiple Attributes, enter terms that contain the appropriate attribute. If you are mapping a Single Attribute, the terms you enter here must match the attribute name exactly. |
| BigPanda Role | Select a BigPanda role from the drop-down menu. |
- Click Create.
SAML Debug Data
You can download recent SAML payloads from the BigPanda UI, which can help with the configuration process and troubleshooting. The past ten login payloads sent from the IdP are available to download in JSON format.
To download a JSON file containing the payloads, navigate to the bottom left corner of the SSO Configuration screen and click the Download SAML Debug Data button.
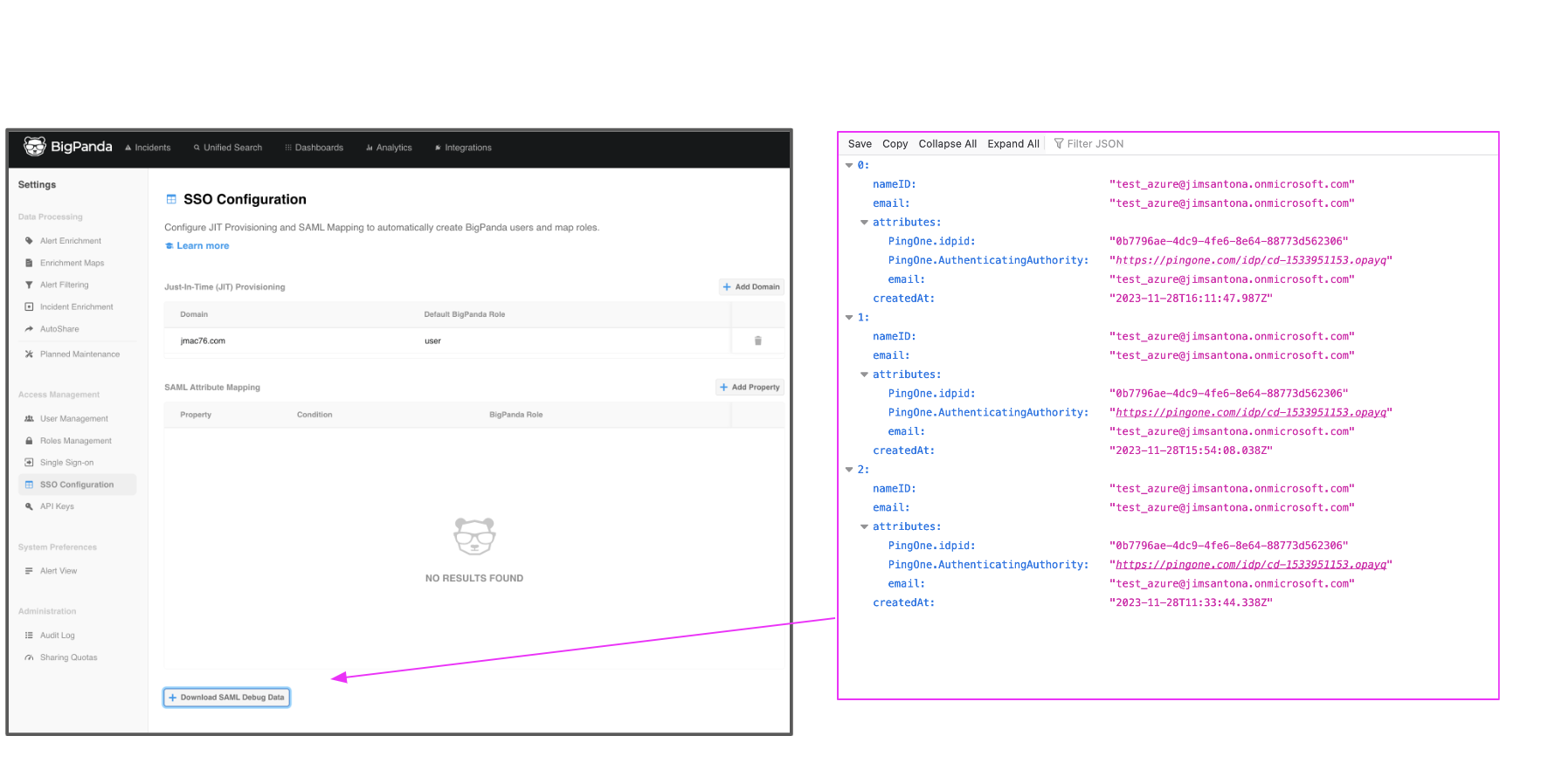
Download SAML Debug Data Button and Sample JSON File
Next Steps
Find Single Sign-On configuration steps.
Learn about User Management in BigPanda.
Learn how to control account access levels with Roles Management.
Updated 4 months ago
