Security
BigPanda leverages a variety of industry-standard security technologies and procedures to protect your information from unauthorized access, use, or disclosure at all stages of the data lifecycle. This ensures that your data is secured at all times whether being transmitted, stored, or processed.
These practices include but are not limited to:
Access granted as per the principles of Least Privilege
Securing data-in-transit using HTTPS/TLS 1.2 and at-rest using AES 256 bit encryption
Secured access via the password-protected BigPanda website or APIs that require token authentication
Activity Logging and Monitoring
Change and Configuration Management
Use of AWS Security tools to protect and monitor production environment
Run in AWS DCs which are certified against industry standard security and compliance frameworks such as ISO 27001/17/18, SOC 2 Type II, PCI, FedRAMP, etc.) For a full list please see the list of Amazon Compliance Programs
In addition to the controls mentioned above, customers have several security controls available within the BigPanda platform to further secure their environment.
Data Transmission
BigPanda adheres to industry standard data processing security protocols, and regularly updates our pipeline to ensure data is handled securely.
Sensitive Data Encryption
All potentially sensitive data in BigPanda is encrypted at rest using AES-256, including passwords, bearer tokens, custom headers, and application keys.
BigPanda uses standards-based methods for all data encryption. For example, passwords are stored in an encrypted format (hashed and salted) using a Bcrypt function as per the Blowfish CipherSpec. Similarly, API keys for supported, third-party integrations are encrypted using AES-256.
BigPanda utilizes AWS proprietary KMS and CloudHSM for key management, leveraging industry best practices, including NIST validated FIPS 140-2 based hardware. Access to KMS and keys is restricted to authorized personnel, monitored, logged, and audited.
Incoming
Standard alert data is collected securely from monitoring systems and sent to the BigPanda service by using one of the following methods:
Webhook—if the monitoring system supports sending data via Webhook, it can be configured to send alert data directly to the BigPanda service via a secure API endpoint.
Agent—if the monitoring system does not support sending data via Webhook, the BigPanda Agent can be configured to collect data locally and send it to the BigPanda service via a secure API endpoint. The agent pulls data from a machine on the local network or cloud infrastructure by using a vendor-supplied API, parsing log files, or using other techniques, depending on the monitoring system’s capabilities.
BigPanda marshals all data sent to the BigPanda service as well as the return codes delivered back to the agent and monitoring systems in JSON.
Outgoing
The BigPanda service sends data to integrated messaging or ticketing systems, such as email, SMS, JIRA, or Slack. BigPanda sends all data to these providers or services via HTTPS and uses industry-standard email and SMS providers.
Access Control
Users in US regions can access the BigPanda application by visiting https://a.bigpanda.io. Users in UK or EU regions can access the application by visiting https://eu.bigpanda.io. All data is sent via HTTPS. Website access requires username and password authentication.
Customer Access
Users can authenticate on the BigPanda website by entering their username and password. Organizations can also configure an SSO integration for user authentication.
BigPanda uses an industry-standard, encrypted token for session-level authentication. BigPanda user passwords are stored in an industry-standard, encrypted hash format. For enhanced security, BigPanda enforces password complexity requirements for all new user passwords and changes to existing user passwords. BigPanda also enforces an automatic session timeout after a fixed period of inactivity.
Two-factor authentication
If your organization does not use SSO, you can request to enable two-factor authentication via emailed links.
To enable this feature, contact your BigPanda account team.
Customers can access only the data for their own organization. Organizations can grant access to users by inviting them into BigPanda.
BigPanda Employee Access
BigPanda personnel access customer data only on a need-to-know basis for support purposes. All support personnel have signed Non-Disclosure Agreements, and no changes are ever made to an account without prior approval from the customer.
Physical Security
BigPanda data centers are hosted on Amazon Web Services (AWS). The IT infrastructure that AWS provides is designed and managed in alignment with security best practices, including the following IT security standards:
SOC 1/SSAE 16/ISAE 3402 (formerly SAS 70)
SOC 2
SOC 3
FISMA, DIACAP, and FedRAMP
DOD CSM Levels 1-5
PCI DSS Level 1
ISO 9001 / ISO 27001
ITAR
FIPS 140-2
MTCS Level 3
Physical access to the data center is strictly controlled both at the perimeter and at building ingress points by professional security staff, using video surveillance, state of the art intrusion detection systems, biometric locks, and other electronic means.
For more information, refer to the AWS Security white paper.
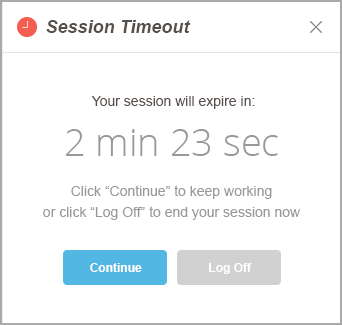
Session Management
For optimal security, BigPanda automatically logs out users when their sessions have been inactive for a long time. The session management feature determines how long a user can be inactive and when a warning message appears for inactive users.
Available Settings
BigPanda enforces the following settings for each user session. If you'd like to customize the settings for your organization, contact BigPanda support.
Session action | Definition |
|---|---|
Session Timeout | Length of time after which the system logs out inactive users—between 15 and 1440 minutes. The default value is 120. |
Session Warning | Length of time before a session times out when a warning message appears—between 1 and 15 minutes. If the session is automatically ended, the user must log in again to access BigPanda. The default value is 2. |
 |
Considerations and Exceptions
The automatic timeout applies only to a specific session. For example, a user may log in from two different browsers and, therefore, have two different sessions. If one session times out, the user is logged out only for that browser. The user remains logged in for the other browser until that session also times out or until the user manually logs out.
Because the BigPanda Dashboard is designed for NOC displays, the automatic session timeout does not apply to it. Therefore, if a user leaves the Dashboard tab open, the user's session remains active.
Data Retention
BigPanda retains customer data for the following amount of time:
Active Customers:
Operational data (such as raw inbound alerts) and other non-analytical data will be deleted after 15 months.
Change data will be deleted after 16 months.
Audit log data will be retained for the contract duration.
Analytical data will be retained for 400 days.
Operational data in Sandbox environments will be deleted after 3 months.
Change data in Sandbox environments will be deleted after 4 months.
Inactive Customers
All data (raw, analytical, and change) will be deleted 3 months after the contract cancelation date.
Alert and change removal
Only resolved alerts and changes marked as done or canceled will be removed once they reach the end of the retention period.
BigPanda Release Process
BigPanda practices Continuous Integration and Continuous Deployment (CI/CD) for building, testing, and deploying software changes. To ensure that new features are tested and released in a consistent manner that does not disrupt existing functionality, we use a controlled software delivery lifecycle.
This lifecycle consists of four phases:
Planning
Implementation
Installation
Rollout
Planning
The planning phase ensures all internal stakeholders are aligned for implementing, testing, and deploying the feature.
BigPanda is committed to constantly improving and incorporating customer feedback into the product. Requests for enhancements (RFEs) are consistently evaluated in the planning phase and deployed into the product to ensure that new features are relevant to your needs.
During planning, decisions about the project scope and rollout are made:
Product Requirements - We refine the functional requirements for the feature to best meet customer needs.
Technical Design - We outline the technical considerations that engineering needs to account for, risks, challenges, and contingency plans for the feature.
Testing Strategy - We identify what a successful release looks like and plan how to validate functionality and stability.
Rollout Plan - We evaluate the risks and impact of feature release and develop a strategy to make the feature available as soon as stability allows.
Before moving to the development phase, the feature must pass through the Development Kickoff Gate. During this checkpoint, we scope the feature to ensure that it will add value and not cause issues for other elements of the product. Once this is complete, development can begin.
Implementation
During the implementation phase, changes are developed and tested at each minor element. Development is split into small development tasks that can be merged into one or more services, ensuring that code stability is tested frequently. As part of the Continuous Integration (CI) process, these code changes are merged, compiled, and tested in a shared repository to ensure the integrity of the code. This process helps identify integration issues early and promotes collaboration among developers.
Most BigPanda releases are controlled with a feature toggle, which allows for easy enablement and rollback of features. This reduces the risk of regressions and allows us to control the order and speed of feature release.
Before we roll out a new feature to testing and internal environments, it is assessed using the Installation Rollout Gate. During this checkpoint, we assess risks and ensure that we can implement the changes without negative impact. If new development is not behind a feature toggle or is high risk, the code will go through additional testing in the installation phase before moving to rollout.
Installation
Continuous Deployment (CD) refers to the installation of software changes to various environments, from staging to production.
Releases that are considered high-risk, because they do not have a feature toggle or may impact core functionality undergo additional testing during Installation to ensure that the release is fully stable.
Once the installation phase is complete, the feature passes through the Rollout Readiness Gate. As part of this checkpoint, we conduct additional stability and quality tests, ensuring that risks have been communicated and the rollback plan is clear. Once this is complete, the rollout will gradually occur.
Rollout
During the rollout phase, the feature is gradually enabled for organizations, starting with low-risk instances. Controlled rollout allows the team to test, monitor, and gather feedback prior to a full-scale release. Our rollout process is designed to mitigate risks, help identify issues early, and allow for adjustments based on user feedback.
Rollout is split into three phases. Each phase can be divided further depending upon need:
Internal - Internal organizations leveraged by BigPanda employees are enabled.
Limited availability (LA) - Showcase organizations, sandboxes, and a subset of production organizations are enabled.
General availability (GA) - The feature is enabled for all organizations. For high-risk or complex releases with dependencies, full rollout may be delayed for a significant amount of time.
Penetration Testing
BigPanda conducts annual third party independent Penetration Testing using Standard Grey Box Assessment Methodology, which includes OWASP Top 10 risks evaluation.
Penetration Testing includes Application Abuse/Business Logic Testing using commercial tools, public tools, custom tools, and manual techniques to identify code patterns indicative of business logic flaws.
Web Application Security Penetration Testing works to identify code patterns indicative of implementation security bugs, including OWASP Top 10 risks, and whether attackers could identify and exploit common and advanced web application security vulnerabilities.
API Security Penetration Testing works to identify a variety of flaws in the code of the client API which could allow for data modification and attack methods through Direct API attacks (attacks against the API end-point itself) and Indirect API attacks (attacks against the app via the API).
Network Security Assessment performs an external vulnerability scan and analysis of the results. Network scans use a vulnerability identification strategy similar to that used by real world attackers.
Our penetration testing is comprehensive and covers the entire CWE list and notes whether all (many hundreds) of CWEs are applicable to to the BigPanda application.
Pen Testing attempts to determine whether attackers could identify and exploit common and advanced web application security vulnerabilities, including:
Cross-Site Scripting (XSS)
Click-jacking
SQL, System Command, LDAP, XML, etc. injection points
Malicious content propagation (use the app as an attack proxy)
HTTP Redirects
Transport encryption verification (Non-SSL for sensitive pages)
Cipher Strength Analysis
Session management subversion
Session Fixation
Response Splitting
Cross-Site Request Forgery (CSRF)
Cookie Analysis
Based on Penetration Test results, BigPanda proactively adds and maintains additional security measures to ensure your data is fully secure. For example, BigPanda has implemented Content Security Policy (CSP) on its websites to protect from malicious cross-site scripting (XSS) attacks and to help prevent code injection and block external references to malicious content.
Security Compliance
BigPanda had undergone an independent third-party SOC 2 Type II security audit on an annual basis, since 2017.
Next Steps
Learn how to set up permissions in BigPanda using Roles Management
Learn how to manage your personal account
Find information about BigPanda's Supported Browsers